SAML (Security Assertion Markup Language) Forward Proxy Tableau is a technology that was developed by Gerard Braad. It is a powerful tool that allows users to securely access Tableau servers without exposing any sensitive data. This technology is particularly useful for organizations that need to share their data with external partners or customers, as it provides an extra layer of security to protect their data.
The SAML Forward Proxy Tableau works by intercepting the SAML requests that are sent by the Tableau server. It then forwards these requests to the identity provider, which authenticates the user and sends a SAML response back to the forward proxy. The forward proxy then sends the SAML response to the Tableau server, which grants the user access to the requested resources.
One of the key benefits of the SAML Forward Proxy Tableau is that it can be easily integrated with other technologies and platforms. For example, it can be used in conjunction with Single Sign-On (SSO) technologies to provide a seamless user experience. It can also be used with multi-factor authentication (MFA) technologies to provide an extra layer of security.
Another benefit of the SAML Forward Proxy Tableau is that it is highly customizable. It can be configured to meet the specific needs of different organizations and can be customized to work with different identity providers and SSO technologies.
In conclusion, the SAML Forward Proxy Tableau is a powerful technology that provides an extra layer of security for organizations that need to share their data with external partners or customers. It is highly customizable, easy to integrate with other technologies, and provides a seamless user experience. If you are looking for a secure and reliable way to share your data, the SAML Forward Proxy Tableau is definitely worth considering. Also, to ensure we spread good content regarding advanced topics!
SAML on Tableau Server can be easy!
SAML implementation is quick and easy when working at an enterprise company, however, it can also take longer when the Tableau Software is a bigger implementation. A lot more to consider.
This guide is for IT, your pro-level Tableau Consultant, and is for those who want to dive in and get dirty. Also, for those who want to get in the code a bit.
We supply the Github link and other helpful information along with your journey.
Tableau Server has many security layers; this is one and a beautiful way to slice it.
Especially when they have a SAML and Tableau Server expert available.
If this is not the case, there’s a desire to use SAML security. Try out
Here at Dev3lop, we have helped companies with the SAML implementation on several engagements, but not enough to make us experts!
Today, we will review an excellent means of SAML forward proxy, Tableau, found on GitHub.
An example of SAML forward proxy in Tableau
Authentication provider as a SAML Proxy for a Tableau Server configured as a SAML Service Provider (SP).
Let’s pause and ensure we cover what SAML is all about!
Learn how to White Board SAML Forward Proxy!
If you’ve had the opportunity to implement SAML with a company, you probably understand the complexities are not for the non-technical Shadow IT team.
SAML Forward Proxy Tableau is not exactly something that roles off the tung and is also a bit advanced to implement! Have you ever had to whiteboard what SAML and Tableau look like? Tableau Server and SAML forward proxy are not for the light at heart!
SAML Explained by Tableau Software
SAML (Security Assertion Markup Language) is an XML standard that allows secure web domains to exchange user authentication and authorization data. You can configure Tableau Server to use an external identity provider (IdP) to authenticate Tableau Server users over SAML 2.0. This allows you to provide a single sign-on experience for your users across all the applications in your organization.
SAML Explained by Wiki
Security Assertion Markup Language (SAML, pronounced sam-el) is an XML-based, open standard data format for exchanging authentication and authorization data between parties, particularly between an identity provider and a service provider.SAML is a product of the OASIS Security Services Technical Committee.
Alternatives for configuring SAML with Tableau Server
- Server-wide SAML authentication.
- Server-wide local authentication and site-specific SAML authentication.
- Server-wide SAML authentication and site-specific SAML authentication. (More at Tableau Software)
Does Tableau SAML affect Workbook Security in Tableau Server?
SAML will not be handling any Tableau Server content security; rather, rather user is going to be authenticated by SAML IDP, not by Tableau Server.
Suppose your SAML guy/gal asks! Be sure to let them know Tableau Server will take care of the heavy lifting.
Let’s continue on our GitHub journey!
SAML Forward Proxy Tableau – GitHub Readme
Tableau supports the HTTP-Post binding for SAML Requests and will always sign the requests.
Some IDPs cannot be configured to support HTTP-POST but only support HTTP-Redirect.
Also, the IDP may not require a signed request.
Usually, signing the Request in Tableau does not alter the ability of the IdP to process the Request. Still, sometimes it is beneficial to reduce the size of the Request so that intermediate servers can store the Request in a cookie.
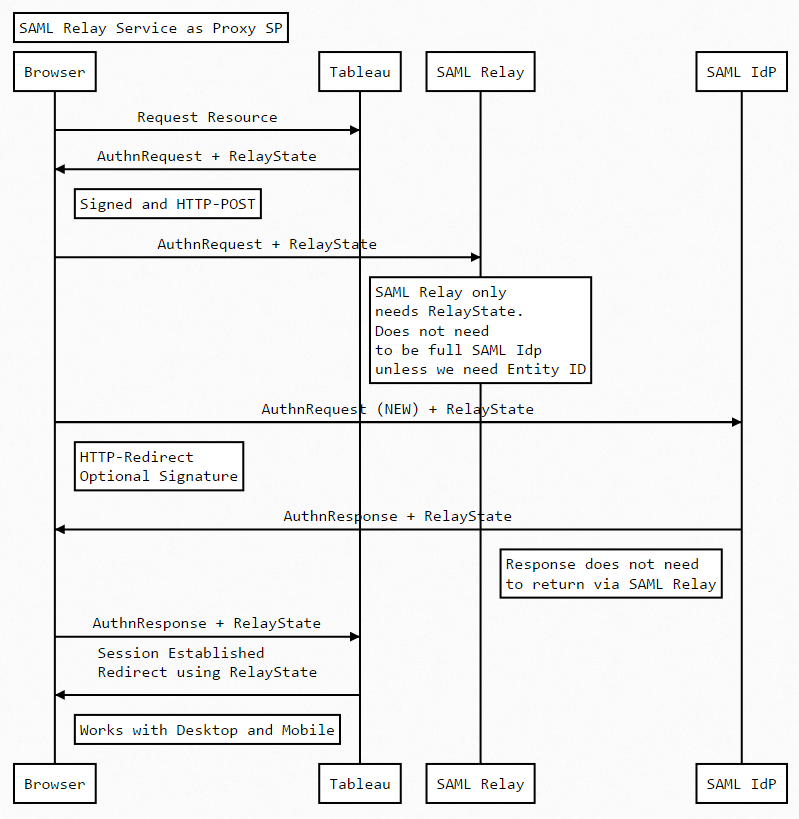
SAML Forward Proxy Tableau – GitHub Proxy runs as the Web Server
This proxy runs as a web server on a port defined in config.js and will work with HTTP or HTTPS. It is effectively a one-way proxy, hence the term SAML Forward Proxy. This example does not proxy the SAML Response. The Response from the IdP is sent directly to the Tableau Server (via the user agent, of course)
Web Sequence:
SAML Forward Proxy Tableau – GitHub Usage
“`bash
$ git clone https://github.com/geordielad/saml-forward-proxy.git
$ cd saml-forward-proxy
$ npm install
$ # Make changes to config/config.js as needed. Add SSL key/cert if needed. Add SAML private key if needed.
$ npm start
“`
SAML Forward Proxy Tableau – GitHub Example List Continued
Run the proxy on localhost with http on port 3000.
Use HTTP-Redirect to the original IDP, and do not sign the Request.
1. Ensure that your IPP is working as expected.
2. Stop the Tableau Server.
3. Get a copy of the IDPS metadata. Note the HTTP-POST endpoint of the SingleSignOnService and change the Location attribute to http://localhost:3000/saml_proxy
4. In config/config.js:
– Update the entryPoint attribute to the original HTTP-POST SingleSignOnService Location.
– Comment out the privateCert attribute. This will ensure that the Request is not signed.
– The example code will update the callback and issuer attributes from the Request sent by the Tableau Server.
SAML Forward Proxy Tableau – Javascript
“`javascript
const fs = require(‘fs’);
module.exports = {
development: {
app: {
name: ‘Passport SAML strategy example’,
port: process.env.PORT || 3000
},
passport: {
strategy: ‘saml’,
saml: {
path: ‘/’,
callbackUrl: ‘https://yourSP.com/saml_callback’, // DYNAMIC FROM ORIGINAL REQUEST – See routes.js
entryPoint: process.env.SAML_ENTRY_POINT || ‘https://youridp.com/entryPoint’,
authnRequestBinding: process.env.SAML_AUTHN_REQUEST_BINDING || ‘HTTP-Redirect’, // Change to HTTP-POST if required
issuer: ‘https://saml_sp_entityid’, // DYNAMIC FROM ORIGINAL REQUEST – See routes.js
//skipRequestCompression: true, // Optional depending on IdP
//acceptedClockSkewMs: -1, // Optional depending on IdP
//disableRequestedAuthnContext: true, //Optional depending on IdP
//privateCert: process.env.SAML_PRIVATE_CERT || fs.readFileSync(‘./tableau_ami_sp.key’, ‘utf-8’), //Uncomment if Request Signing is required.
//cert: process.env.SAML_CERT || fs.readFileSync(‘./okta.cert’, ‘utf-8’) // Not needed because we are not processing AuthnResponse
}
}
}
};
“`
SAML Forward Proxy Tableau – GitHub Example List Continued
5. Start the proxy if necessary. npm start.
6. Restart the Tableau Server and test the proxy by calling your Tableau Server in the Browser. View URLs and any public pages (for example, sites and projects) will work as the proxy will forward the RelayState.
7. test the SAML Forward proxy with Tableau Desktop and the Tableau Mobile App. They should work as expected.
This example code has been tested with Okta and Azure AD.
SAML Forward Proxy Tableau – Community Rocks
Another solid find in the Tableau Community world. I am thrilled to share this with our audience and, hopefully, more future Tableau SAML implementations!























